THORChain hacked for third time in a month, with A$11m stolen

Pic: Stevica Mrdja / EyeEm / EyeEm via Getty Images
THORChain has been hacked for a third time in the past month, this time with the attacker managing to drain nearly A$11 million in cryptocurrency from the crosschain crypto-asset bridge.
The project was also hit with an exploit last week that drained A$7 million in crypto from its systems, In late June an attacker managed to steal US$140,000 (A$190,000) in funds.
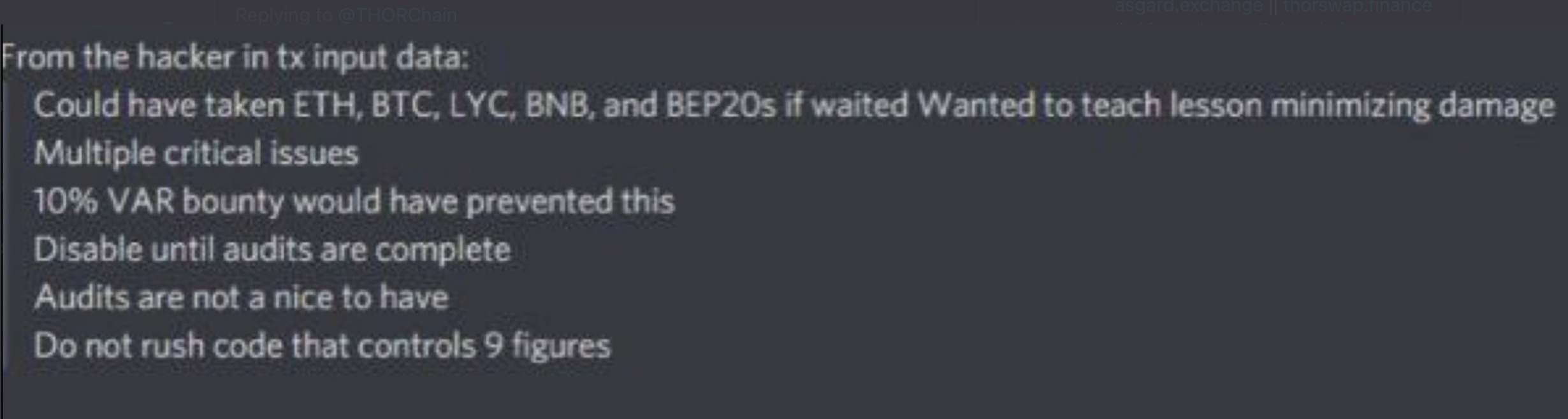
The hacker using this latest exploit left a message in the transaction data boasting he or she could have stolen more.
“Wanted to teach lesson minimizing damage multiple critical issues … Audits are not a nice to have. Do not rush code that controls 9 figures.”
On its Twitter feed, THORChain said that the attacker used a “sophisticated attack” but seemingly limited their damage, “seemingly a whitehat”.
The whitehat requested a 10% bounty – which will be awarded if they reach out, and they should be encouraged to do so.
It is a tough time for the community and project, and the pain is real.
The treasury has the funds to cover, but it’s time to slow down.
— THORChain (@THORChain) July 23, 2021
It was promising to press on despite the massive setbacks.
It easy to pile on the project currently.
There were really only two options. Launch and accept the risk of issues, or not launch and stay in the 90% complete audit-review cycle for another 6 months.
Both are difficult.
— THORChain (@THORChain) July 23, 2021
This isn’t going to break the project or change its vision.
The network will stay halted until all Bifrosts can be reviewed.
If you would like to help please reach out.
— THORChain (@THORChain) July 23, 2021
THORChain uses smart contracts to enable swapping crypto-assets across different blockchains. (Generally decentralised exchanges are limited to a single blockchain, like Ethereum).
Most of its team are anonymous.
At 4.40pm AEST, THORChain’s RUNE tokens were down 8.6 per cent to $US4.02, giving the project a market cap of US$941 billion. That still makes it the No. 71 crypto.
Related Topics
UNLOCK INSIGHTS
Discover the untold stories of emerging ASX stocks.
Daily news and expert analysis, it's free to subscribe.
By proceeding, you confirm you understand that we handle personal information in accordance with our Privacy Policy.








